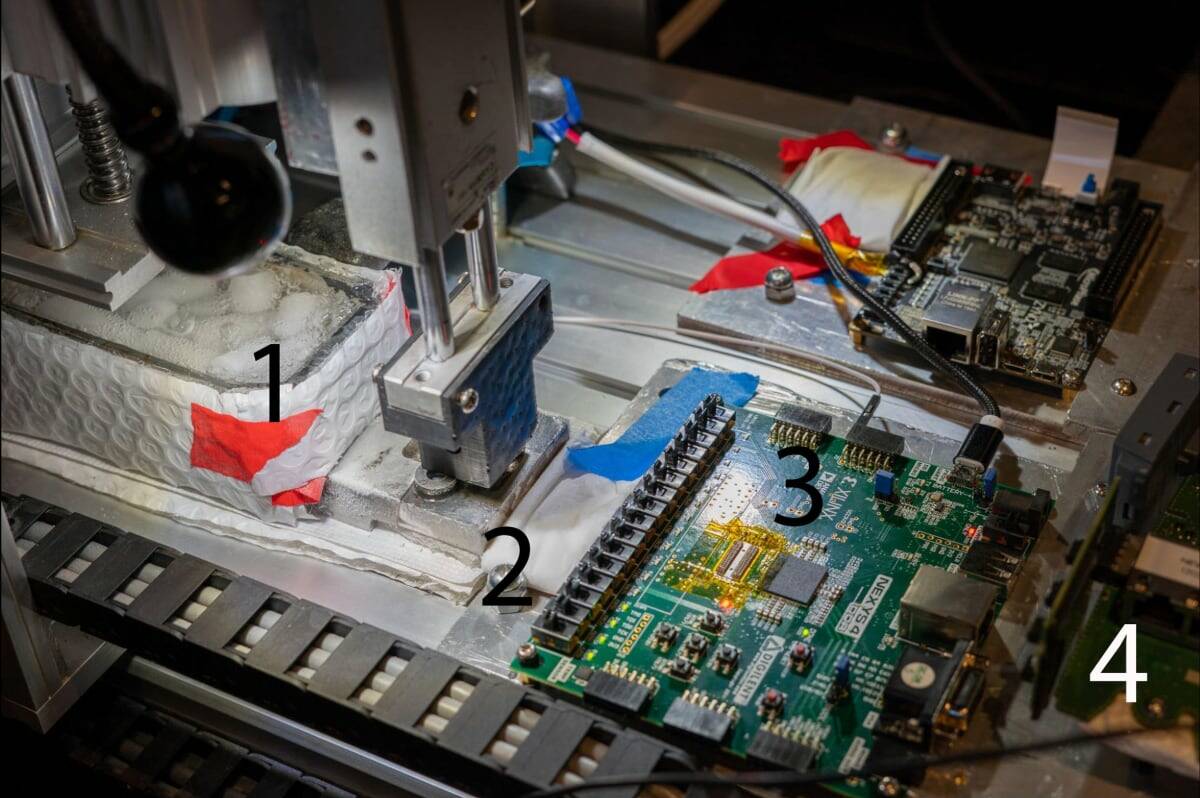
WithSecure™ on Twitter: "@nxsolle What's a cold boot attack? It starts with an attacker getting their hands on a laptop. https://t.co/r14cDD8M1O https://t.co/kgUht2491L" / X

Cold Boot Attack Method Leaves Laptops Vulnerable | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More
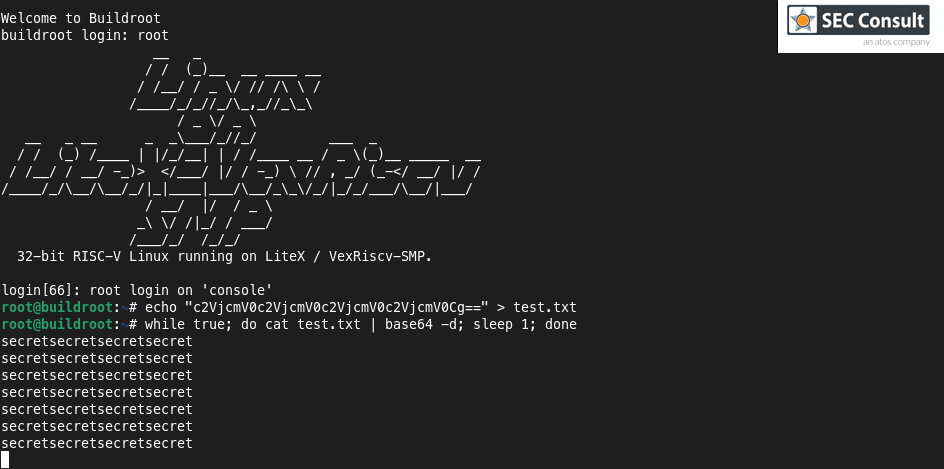
![PDF] Cold Boot Attacks are Still Hot: Security Analysis of Memory Scramblers in Modern Processors | Semantic Scholar PDF] Cold Boot Attacks are Still Hot: Security Analysis of Memory Scramblers in Modern Processors | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d85f103b1b12c0b82d9d3625e61ff41b80b7efc9/4-Figure2-1.png)